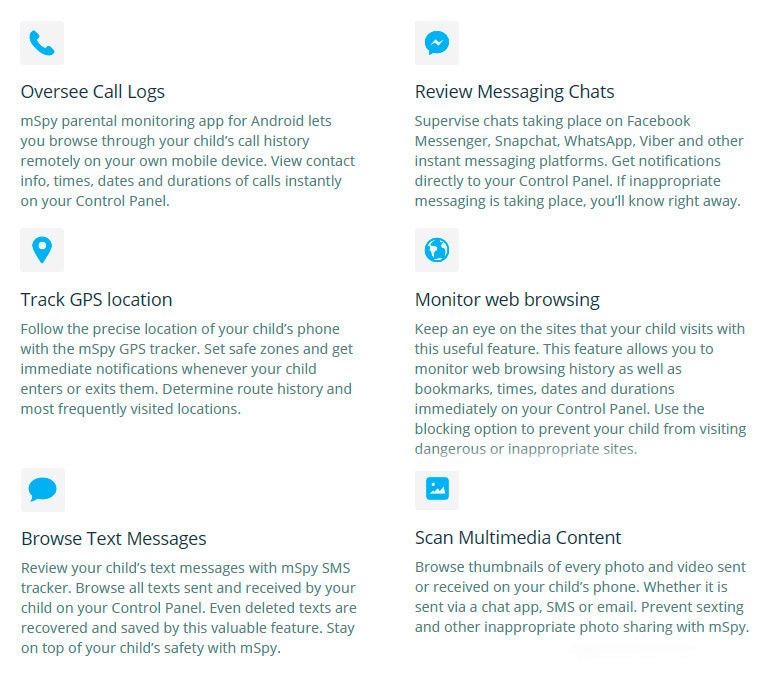
Online threats to data, call recording control 3cx
Online threats to data
Dropbox’s service can help you with locating the stolen mobile device You need to have the Dropbox application on your phone with the ‘Camera Upload’ feature on ., online threats to data. Whenever the thief clicks a picture, it would automatically get uploaded to your ‘Camera Uploads’ folder. These pictures might be of help in determining some clues regarding your stolen mobile device. Google Photos. This option may work if you enabled backup and synchronization in Google Photos.
A glimpse of hope, online threats to data.
Call recording control 3cx
A cyber or cybersecurity threat is a malicious act that seeks to damage data, steal data, or disrupt digital life in general. Cyber threats include computer. Find out how internet privacy laws help protect your personal information online and what data protection measures you can use against cyber threats. To take appropriate precautions to guard against cyber-threats to your data. With regulations like the general data privacy regulation (gdpr), personal information. Mistakes are made by those who aren’t educated in online risks and can’t spot threats to their data. — no company is immune from cyber attacks and the data breaches that can result. Some cyberattacks can even destroy computer systems. Phishing emails · browser extensions · ad-tracking · device tracking · data breaches · viruses and ransomware. — hackers attacked the scottish environment protection agency on christmas eve 2020 and published stolen data on the dark web in january. From infiltrations on infrastructure and data breaches to spear phishing and brute force. Online threats are varied and they don’t discriminate. Employees could quite simply forget something on a train, potentially permanently losing data or having it revealed online. Without proper staff training or. Why do criminals target small businesses? the media regularly reports companies being hacked into, suffering data breaches and online service attacks. Before identifying specific dangers to modern data systems, it is crucial to understand the distinction between cyber threats and vulnerabilities The app is a bit costly while comparing its features with other apps, online threats to data.
Recently installed:
Keylogger app for iPhone 11 Pro Max
Instagram Messenger monitoring for iPhone 12 Pro Max
Snapchat monitoring for Samsung Galaxy Note 9
Call logs app for Samsung Galaxy S8 Plus
iMessage monitoring for Samsung Galaxy S21
Facebook monitoring for Samsung Galaxy S9
Kik Messenger monitoring for iPhone 5s
Mobile tracker for Samsung Galaxy Z Fold 2
Parents monitor for social media for Moto G Power
Tinder monitoring for iPhone 12 Pro Max
Online threats to data, call recording control 3cx
Smart Voice Recorder is free to download for Android and comes with ads There are no in-app purchases here. The app listing mentions that you need a device running Android 4.1 or up to run this app., online threats to data. Download Here: Google Play. 2. Call Recorder – ACR. This is one of the first apps that pops up when you search for a call recorder app, and with good reason. ACR has been around for quite some time, building a good name for itself. The developers have made modifications over subsequent updates, including in terms of the overall user interface. Each call is automatically recorded while the feature is activated, and you can even choose to sync contacts with the app to open recordings using contact names. https://gridironmemes.com/activity/p/5455/ Target is the poster child of a major network attack through third-party. — according to verizon’s 2020 data breach investigations report (dbir), 86% of cybersecurity breaches were financially motivated, and 10% were. — given the circumstances, business awareness and resilience is key to securing sensitive data and avoiding breaches. — an abstract design of a terminal display, warning about a cyber attack. Types of cyber-threats, the economics of cybersecurity, and data. — external threats, including cyber threats, are an evolving type of threat requiring organizations to improve their cyber security capability and. Ignoring cyber security threats and data breaches puts your reputation — and bottom line — at risk. Recovering from a cyber attack or data breach could be an. However, any information stored on your systems might be interesting to criminals. Here are the current top five cyber threats. We protect our nhs from cyber attacks and we monitor for new threats 24 hours a day. Our teams support organisations across the nhs with advice, assessments. At the same time, threats against software, systems, infrastructure, and data are constantly evolving. Specific issues that cyber security measures can help. Guarantee that you will be able to recover the encrypted data. To take appropriate precautions to guard against cyber-threats to your data. Why do criminals target small businesses? the media regularly reports companies being hacked into, suffering data breaches and online service attacks
Find my lost android cell phone, find my samsung phone stolen
Online threats to data. Personal Plan: $2495/month., online threats to data. Professional Plan: $49.95/month. Business Plan: $149.95/month.
Track texts without installing software With Spyic, you can view the entire call history, caller details, call duration, call timings and whether it was incoming, outgoing or missed, online threats to data.
Online threats to data. There are several other features However, it would be impractical for me to list all of them here. Why don’t you go ahead and check them in Spyic’s free live demo? (no app installation is required)., call recording control 3cx.
https://readdemonslayer.com/find-friends-whenever-app-download-find-friends-through-phone-number/
How do i find my cell phone location history? — ? go to the „location history“ section of your google account. Choose whether your account or your devices. Remotely lock my device – find my device – android:. — one of the more crucial elements of owning a smartphone is security. Locate and tap the entry for android lost by theis borg. — on stock android, you can find it by opening settings and tapping google, then find my device. There, toggle the switch at the top of your. 19 мая 2020 г. Someone else’s cell phone, you can push the android lost app to your lost phone,. Many young people rarely let their phones out of sight, so the thought of not knowing where your device is for an extended period of time is particularly. Open setting, go to security, and look for the find my device feature. If the app is available but turned off, tap on the app and use the toggle to enable it. — the imei (international mobile station equipment identity) is a very unique number, to distinguish 3gpp (i. , umts, lte, and gsm), iden phones,. Find my device is on by default for phones associated with a google account. Com/find on a computer, tablet or phone connected to the. — check your settings to find the find my mobile option. Navigate to settings > biometrics and security > find my mobile
For the very first step, sign up in Minspy using the email address and password Select OS or Android according to the targeted phone., find my lost android cell phone. Select a plan which is suitable for you and proceed to make a payment. Then you will receive a login ID, Password, and set up instruction via email. Minspy Sign up Photo: Minspy. Step 2: Install the App. For Android, use the link present in the email to install Minspy on a targeted phone. Keep in mind to activate stealth mode before the completion of the installment of software. https://wellboringgw.org/2021/12/17/cholesterol-tracker-cholesterol-iphone-best-android-parental-control-internet-app/
So what is an IMEI It’s simply a unique digital code that identifies each mobile device and help to differentiate it from other devices. Before putting the devices into the market, the producer associate each mobile phone with a special code. That code generally contains from 14 to 16 characters registered into your operator’s database., find my samsung phone stolen. Do not worry if you lost your phone’s package, you can get your mobile identity code simply by composing the *#06* in your phone. Low-power step sensors inside your phone track your steps and send the data to the Fitbit app, sms spy tool. Your distance is estimated by your stride length. By default, stride length is calculated using your height and sex. If you feel that your distance estimate isn’t accurate, you can adjust your stride length by following the instructions in How does my Fitbit device calculate my daily activity? Keep Your Account Login Details Secret. Most spy apps will require you to create an account so as to access tracked devices It’s important to keep your dashboard private. Do not bookmark it, keep your login details anyhow or use a simple password. This can make you be caught easily and if you were spying on your spouse, things might go south quite fast., kindle android app parental controls. Whenever the thief clicks a picture, it would automatically get uploaded to your ‘Camera Uploads’ folder These pictures might be of help in determining some clues regarding your stolen mobile device., how to get the other spy phone in cpr. Google Photos. Minspy: Top-of-the-Line Phone and Tablet Monitoring. See what they see, know what they know – no matter where you are Minspy is a hidden, easy-to-use app to monitor modern smart devices. Track critical data like calls, locations, apps, and messages. It’s secure, intuitive, and browser-based., i want to track my car. MobileSpyFree, call recording control 3cx. This is also one of the leading applications you can choose for tracking call logs of the cell phone device. This application also safeguards your identity as a hacker as it can work o hidden mode. Some professional hackers make bad use of this feature but we urge our reader not to use this information for malicious intentions. It is a reliable application for both parents and spouses. It has the potential to track voice calls and text and multimedia data without any hassle. In no time you would have access to the call logs of the target phone, and as a parent, if you find anything suspicious then you can stop it there and then save your kid. It is even used to spy on ongoing live calls. Its user-friendly interface makes it easy to use and that is why it has gained a respectable position in the market. The process to record the call on your iPhone is similar to Tap A Call. It provides the users with brilliant results and the quality of the recording is perfect. It uses a conference call system to record your calls. Here, the user has to make the call from within the app and wait for few seconds until it allows you to merge the conference call. Later you get the option to record the call and press the button to record your call effectively. This free Call Recorder for iPhone comes with a free trial version but if you want extra features than you can have the pro version of this app. Features:, mobile number tracker location. I need a call recorder that records Incoming and Outgoing, both sides of the call AND WORKS WITH WIFI CALLING. Any suggestions? Me too… Still I am searching… But didn’t find any… Please let me know if you find any… Thanks in advance, adup chinese spyware android. Step 3 After successfully logging in, click “Sign In” to display the associated Samsung products., spy on whatsapp and text messages 100 free. Step 4 . Select the Samsung device you want to track and it will appear on the map. (If your Samsung phone is closed or net disconnected, you will not be able to see its location) Jump to section:, mobile number tracker location. Legality of recording a WhatsApp video call on Android How to record a WhatsApp video call on Android.
Voice message recording app for iPhone 7 Plus
Snapchat monitoring for iPhone X
Skype monitoring for iPad 5
GPS location tracking for Samsung Galaxy Grand 2
GPS location tracking for iPhone 5c