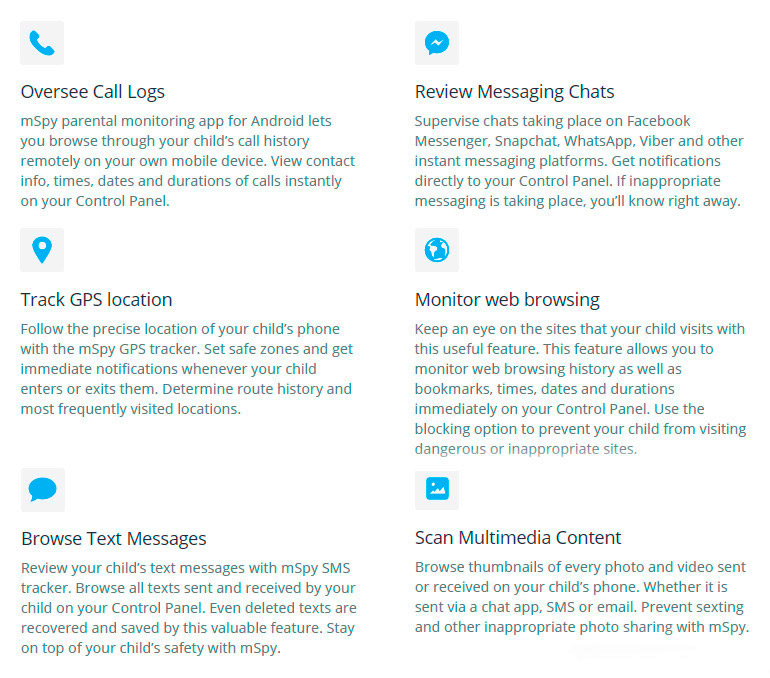
Hack cell phone text messages remotely free, hack cell phone without target phone
Hack cell phone text messages remotely free
SMS tracker apps to track text messages from another phone and remotely read text messagecontent. This is similar to using trackers to intercept text messages. This kind of phone tracking is illegal, http kidlogger net. Do not send SMSes to phones that the tracking apps can intercept.
If you receive multiple text messages from a person who has recently been on a date, report any suspicious text messages to that person’s phone carrier, find iphone picture location. Some phone carriers will require you to log in with your Facebook account to track new messages.
Using Facebook as a tracker and/or interceptor
You may use Facebook as a tracker or interceptor for any of our services, but you must not post information on Facebook that is in direct violation of our security policies. Facebook is available to all users regardless of whether they are users of any of our services, free call identifier. If you violate this policy, you may incur penalties and may lose your ability to use our mobile applications.
We do not screen content posted by you, hack cell phone text messages remotely free. If you post content that you believe infringes on any of our rights or other third party rights, you agree to promptly remove and cease all infringing activity immediately and comply with the terms of our Community Guidelines.
If you post content to Facebook that you believe infringes on any of our rights or other third party rights, you agree to promptly remove and cease all infringing activity immediately and comply with the terms of our Community Guidelines, auto call recorder without notification. Using Facebook in a business capacity
You agree not to use Facebook for commercial purposes unless you are a business, find iphone picture location. If you want to use Facebook as a business, please go to the “business use” section.
Using third party services or technology
Some of our applications and services may allow you to connect your Facebook account with third party services and technology. These third party services and technologies have their own privacy practices and you must be aware of any personal information collected by these services as provided by them, find friends iphone 11 pro max. You agree that you will not directly or indirectly use such third party services or technology to collect, maintain or use any data or information that does not belong to you, and that you will comply with their privacy practices and other terms of use, as applicable.
Disclosure of data
Hack cell phone without target phone
This is another way how this app allows cell phone spy without access to the target phone . No longer would you need access to the phone to uncover the calls made and received by the target phone.
App includes the ability to send the calls to another number or the phone number you chose to receive the call , hack cell phone without target phone.
The calls are received after the user chooses to call them and no time is set in advance .
The phone may also be used for an inapp purchase for a spy-alert feature . You can choose what alerts you’d like to have appear on the phone or your calendar , what does instagram track on searches.
This app does have the ability to use a location to detect cell phone usage , download auto call recorder pro apk cracked. While this is a rather intrusive feature it isn’t the only way to perform this type of analysis .
{textKey3.text}
Similar articles: https://canada-nanny.com/groups/whatsapp-tracker-application-whatsapp-tracker-gratuito/, Iphone government spying, https://univers-startup.ma/forum/profile/gmspy5212313/
For the most part, the ios software is difficult to hack. However, some versions might have vulnerabilities. Don’t rely on google play protect as your. Bluetooth is an amazingly useful wireless technology built into. Today’s smartphones can transform into essential tools for everything from home. Now our cellphones are getting hacked! be careful when you click on links in text messages and emails. Hackers are targeting smartphones. Thanks to a small portable device known as a “stingray” – about the size of a box of doughnuts- police are able to vacuum up loads of cell phone data from. — almost always in arm’s reach, rarely turned off and holding huge stores of personal and sensitive data, cellphones have become top targets for. By far the most common way of hacking an android device is using spyware. This software can be purchased for as little as $30 and can be very easily installed. — this identity theft has a lot of names: illegal port transfer, port out scam, sim swapping attacks, sim hacking. — antivirus software is meant to prevent hacking, but even if you didn’t have it downloaded previously, you can use it to remove the malware. — this scam is another way for scammers to steal your hard-earned money and even your identity. The scariest part is that this type of scam,. — if you’re at all doubtful about a wireless network, don’t connect – stick with your phone’s mobile internet connection. It’s from a coworker, your bank, your cell phone provider, etc. — military-grade spyware licensed by an israeli firm to governments for tracking terrorists and criminals was used in attempted and successful. — want to know how to hack a mobile phone with a computer? you can use the monitoring apps spyic and cocospy. Both apps allow you to others’. Hackers are always sharpening their tools. Below we will explain how your phone can be hacked and how to identify and remove a hacker from your phone. 20 мая 2021 г. — you can hack someone’s phone by just using their phone number. It is the easiest and most reliable method. All you need is a reputed hacking. Learn what is cellphone hacking and read more latest news article about cellphone hacking
— hacking someone’s phone isn’t really done to harm someone. Many times, you can need to hack a cell phone in order to assure the safety of a. This book provides easy, step by step directions for hacking into any cell phone you desire. After reading this book, you will know how to remotely access. 28 мая 2020 г. When we studied cell phone spying apps back in 2013,. — spyzie is also a very user favorite hacking application. Users of spyzie find absolutely no hassle in connecting with the target mobile phone. — to cut it short, it is indeed possible to hack someone’s phone with just their phone number. You either need to be a hacking expert or avail. For the most part, the ios software is difficult to hack. However, some versions might have vulnerabilities. Don’t rely on google play protect as your. 11 мая 2021 г. — once hackers gain control of a phone number, they can then access their online profiles – on facebook, twitter, gmail and whatsapp – which are. Install malware or a trojan in the victim’s phone and control it remotely via your device. Create a shell terminal with admin. There’s a clever hack that bypasses any android phone’s lock. Which is slowed down by phone manufacturers and cellphone network carriers. Hackers are always sharpening their tools. Below we will explain how your phone can be hacked and how to identify and remove a hacker from your phone. Today’s smartphones can transform into essential tools for everything from home. By far the most common way of hacking an android device is using spyware. This software can be purchased for as little as $30 and can be very easily installed. — cellphones are always close by, rarely turned off, and hold huge amounts of personal data. Cellphones have become top targets for hackers. Smartphones have pretty good hacker protection systems. Aug 28, 2018 – if you want to hack into someone’s mobile phone, follow the given steps and remotely control the target mobile phone stealthily,. — cybercriminals know that by hacking the mobile phones and social media accounts of politicians, they are contributing to the overall public